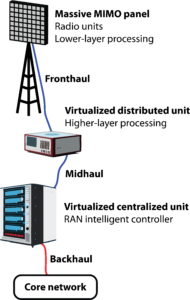
The 3GPP standard for mobile communications only specifies the basic functionalities needed to make a device from any vendor (e.g., Apple, Samsung, Xiaomi) communicate with network infrastructure from any vendor (e.g., Ericsson, Nokia, Huawei). The exact implementation details (e.g., hardware and algorithms) can be selected freely—a setup selected to promote innovation and competition between vendors. Since the internal interfaces (blue cables in the picture) between radio units, lower-layer processor units, and higher-layer processor units are unspecified, a telecom operator must buy its entire radio access network (RAN) from a single vendor.
Single-vendor networks have several inherent benefits: jointly optimized hardware and software, ease of deployment, and clarity of who to blame when something fails. However, it also leads to vendor lock-in, where the operator has little bargaining power when buying new equipment and cannot benefit from new innovations made by other vendors.
Motivation for Open RAN
Today, there are only a few vendors capable of delivering a complete network, and recent geopolitical developments have reduced the viable options in each country even further. To create more options and market competition, the O-RAN Alliance has since 2018 worked to define what components a network must contain (e.g., radio unit, distributed unit, centralized unit) and specify open interfaces between them (e.g., fronthaul, midhaul, and APIs). This is called the Open RAN specification, and it is meant to enable new companies to enter the market and specialize in offering a limited number of components. If successful, this will allow operators to mix-and-match hardware and software from multiple vendors in the same network.
There has been much hype about Open RAN and the innovations it might bring over the past few years. Several people have even tried to convince me that future networks cannot work without it. Nevertheless, six years into the Open RAN era, there are barely any multi-vendor networks, and many people were surprised when AT&T decided to build a new nationwide Open RAN network that only consists of $14 billion of Ericsson equipment. This has been called “Single-vendor Open RAN” and has led to claims from independent experts that Open RAN is failing miserably [see: Light Reading, May 2024; telecoms.com, Aug 2024].
Success criteria for Open RAN
I think the Open RAN development mostly goes as intended, even if promises made in various press releases are yet to be fulfilled. The RAN technology is highly complex, so one cannot expect new vendors to be able to compete with the traditional giants immediately. A mix-and-match network using hardware and software from new vendors will likely not provide competitive performance any time soon. This is reminiscent of how Apple has tried for years to build high-performing 5G baseband chips for their phones but is still far behind Qualcomm.

The potential success of Open RAN should not be measured by the number of new multi-vendor networks being deployed in the next few years but by how the increased competition and intelligent network virtualization lead to cost reductions for the operators—both when deploying new networks and later when network components must be replaced due to hardware failures or upgraded with new functionalities. It will naturally take time for these potential benefits to materialize because most operators have already deployed traditional 4G and 5G networks and will not invest in new ”greenfield” deployments anytime soon. Perhaps the first large-scale multi-vendor deployments with hardware from untraditional vendors will take place in geographical regions currently lacking 5G connectivity and where cost savings are more important than top-of-the-line performance. In many other places, I believe Open RAN will not be a commercial reality until 6G networks are rolled out.
The O-RAN Alliance identifies four benefits of Open RAN: openness, interoperability, virtualization, and AI automation. Single-vendor Open RAN compliant networks will use the latter two benefits from day one to reduce hardware/operational costs and enable new services. The operators might also benefit from the former two in the long run, particularly for components that become commodified. Virtualization and AI automation are, of course, features that a state-of-the-art closed RAN deployment also supports—they are not unique features for Open RAN but have been researched under the “Cloud RAN” name for a long period. However, AT&T has demonstrated that there is little incentive to build new networks in the traditional way when one can get openness and interoperability as well.
In conclusion, Open RAN is successful in the sense of being a natural feature in any new network deployment. However, the hyped interface openness and multi-vendor support are not the transformative aspects, and we cannot expect a major uptake until greenfield 6G deployment commences.